Comodo
Securing your Infra is easy with cyber safe.
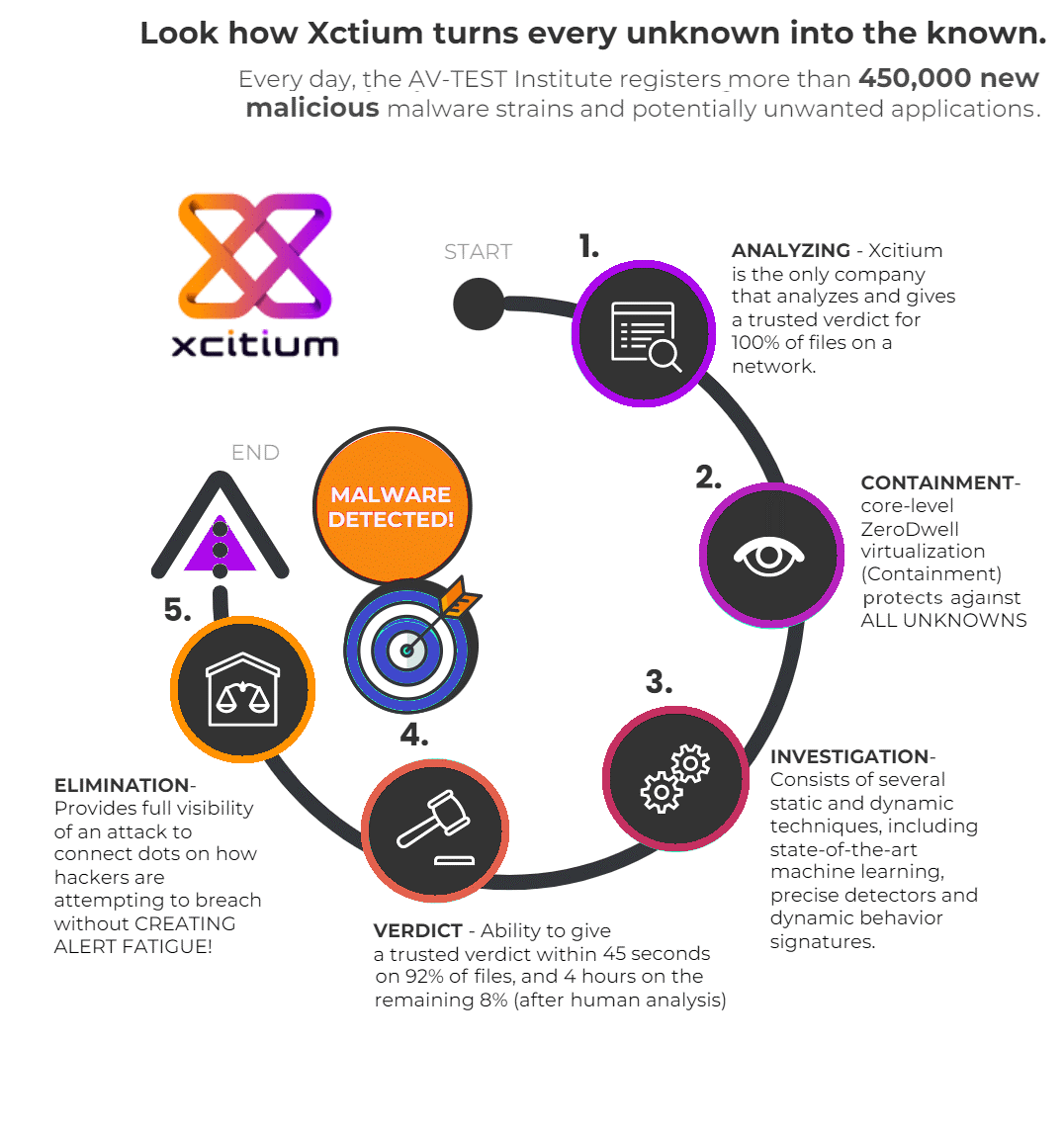
OpenEDR is an open source threat detection and response platform you can use to protect your endpoints. Offered for free, OpenEDR provides real-time analytics, and full MITRE attack-progression visibility with threat event correlation and root cause analysis. Use OpenEDR to protect, detect, and remediate adversarial activity and attacker tradecraft. This advanced EDR telemetry platform is accessible to all cybersecurity professionals, and every sized business or organization, for continuous monitoring and advanced cyber defense.
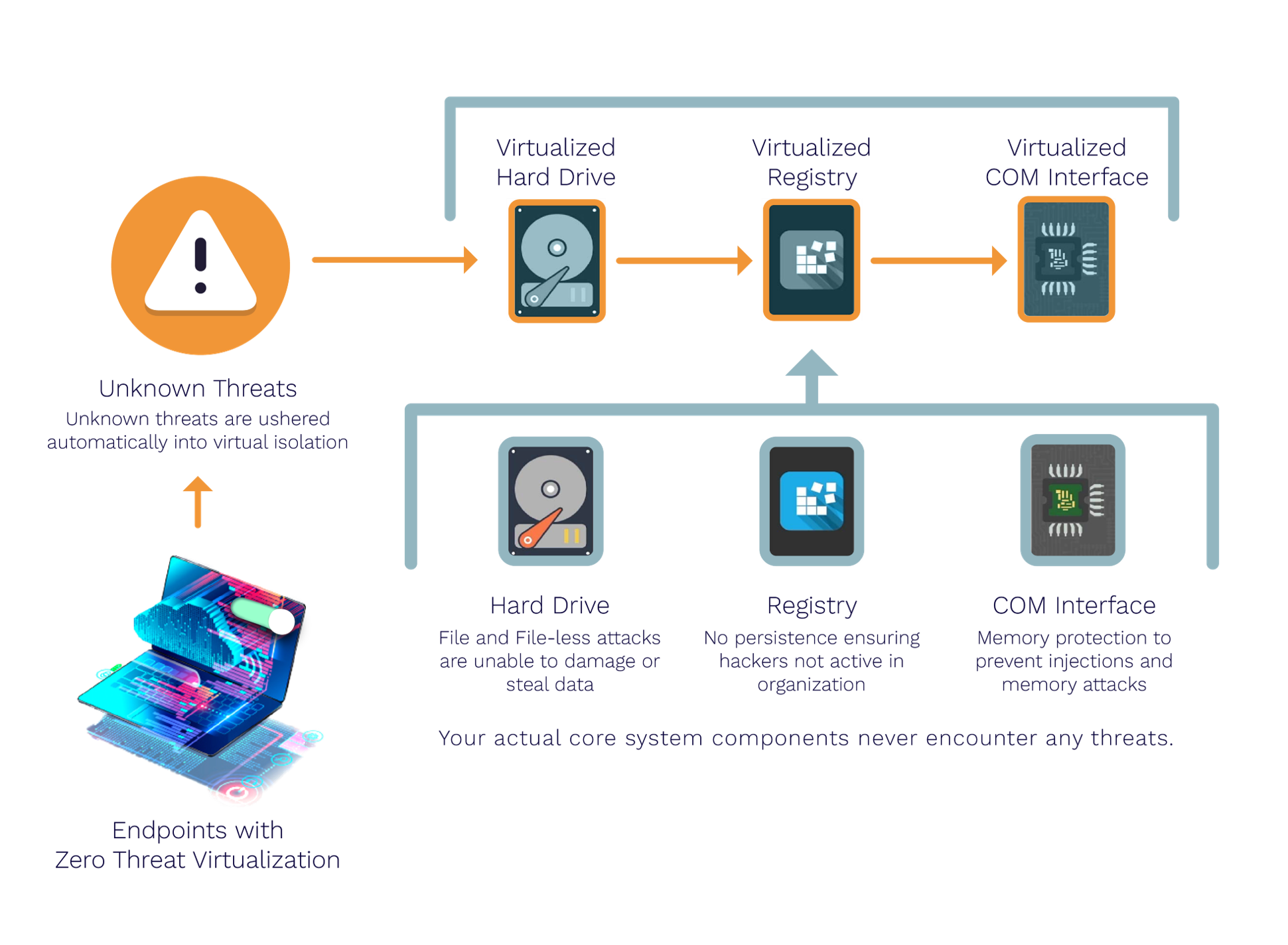
ZeroDwell Xcitium Advanced EDR technology delivers auto-isolation services that complement your existing endpoint protection platform or security posture. This Advanced EDR standalone product includes a SaaS management console, endpoint client agents, Advanced EDR service delivery from the Xcitium Threat Research Labs (XTRL), and the Verdict Cloud engine, a file safety determination service used to assess isolated files and objects to EDR provide a malicious or safe verdict about contained Unknowns.
EDR
EDR is often called Endpoint Detection and Threat Response (EDTR). Both labels represent essential cybersecurity technology that helps organizations continuously monitor all their endpoints to detect, analyze, and respond to cyber threats such as malware and ransomware attacks. It includes a cloud-based application that monitors the endpoints and correlates telemetry data, and then provides analytics to the organization's security teams. EDR technology helps detect and respond to advanced threats on endpoints to prevent the attack from causing damage.
Main Functions of an EDR
1. Endpoint Detection: The programs are designed to detect malicious activity on endpoints, such as computers, laptops, and other devices connected to the network. This includes identifying malicious files, suspicious network traffic, and other indicators of compromise.
2. Threat Hunting: The solutions are designed to help security teams hunt for threats and investigate suspicious activities. This includes identifying malicious files, suspicious network traffic, and other indicators of compromise.
3. Incident Response: The solutions help security teams respond quickly and effectively to security incidents. This includes identifying the incident's source, determining the incident's scope, and taking steps to contain and remediate the incident in Endpoint Detection Response.
4. Forensics: The solutions are designed to help security teams collect and analyze evidence from endpoints to identify the root cause of an incident. This includes collecting system logs, memory dumps, and other artifacts from the endpoint.
5. Compliance: EDR solutions are designed to help organizations meet regulatory and industry compliance requirements. This includes identifying and remediating vulnerabilities, implementing security policies, and monitoring for suspicious activity.
End Point Manager
Practice cyber hygiene to reduce the attack surface by identifying applications, understanding the vulnerabilities and remediating patches.
Proactive updates for optimal security
View patches needed on devices, applications, and operating systems communicating with Endpoint Manager. Consolidate time, resources and efforts by centralizing your activities into one simple to use patch management system.
Keep your endpoints up to date
Protection against zero-day web threats, without hindering employee productivity. Detect 100% of unknown fileless threats with Xcitium's intelligent file analysis engine. Apply our recommended policy, created upon a meticulous examination of threat behavior analytics.
Discover, Audit, Compliance-all-in-one
The dashboard shows real-time data about the operating system, connection status and security posture of all devices enrolled to Endpoint Manager. The dashboard also lets you view threat results, notifications, and generate reports.