WALLIX
Securing your Infra is easy with cyber safe.
The WALLIX solution suite is flexible, resilient, quick to deploy and easy to use, and WALLIX is recognized by industry analysts (Gartner, Kuppingercole, Forrester, Frost & Sullivan) as a leader in the field of privileged access management. help organisations reduce cyber risks, embrace innovation and disruptive technologies securely, manage flexibility and cost, and improve operational resilience.
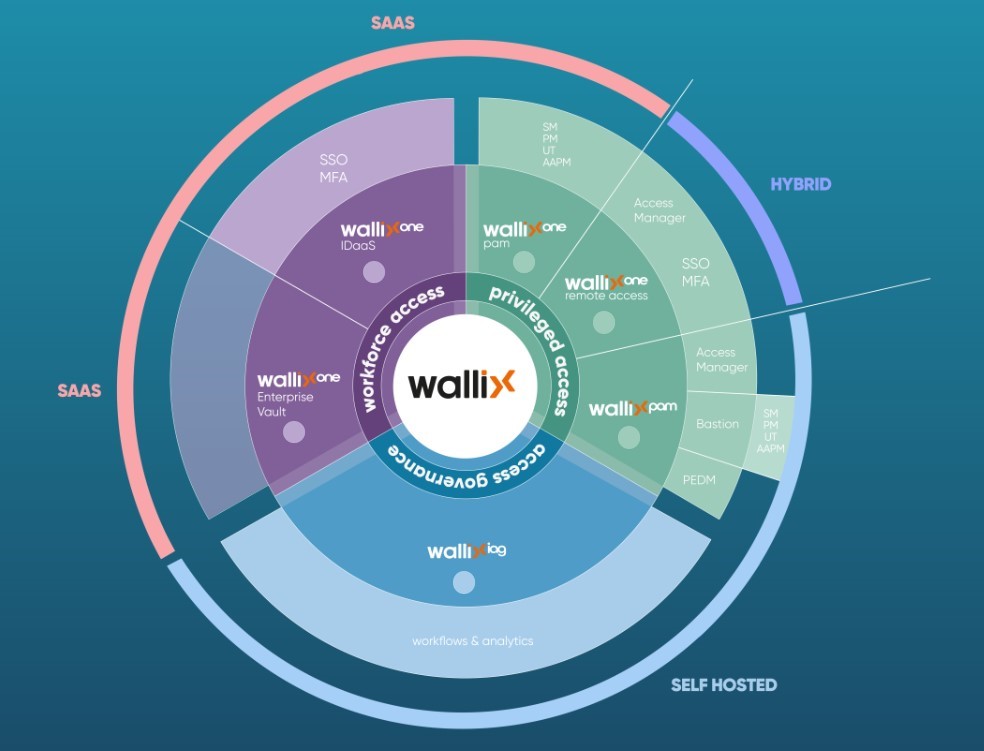
Solutions
Wallix PAM
Privileged, administrative, or overly empowered accounts are consistently among attackers’ main targets and frequently lead to major breaches. Leaders overseeing identity and access management should be implementing privileged access management (PAM) to protect these critical accounts.
WALLIX PAM is designed to manage and secure privileged accounts within an organization’s IT and OT environments. Privileged accounts are those with elevated permissions used by people often held by administrators, IT personnel, or third-party vendors, but also software and machines, that provide access to critical systems and sensitive data.
WALLIX PAM focuses on controlling, monitoring, and securing access to these privileged accounts to mitigate the risk of unauthorized access, data breaches, or misuse of sensitive information.
Overall, WALLIX PAM aims to strengthen an organization’s cybersecurity posture by managing and securing access to critical systems, reducing the risk of insider threats, and ensuring compliance with regulatory requirements.

Remote Access
Secure Remote Access provides control and governance over remote access to secure corporate IT assets and infrastructure. It enables businesses to seamlessly interact with third-party providers without compromising security.

Ease of Use
With no VPN to install and manage, the ability to delegate administration to business owners Remote Access relieves IT teams from unnecessary requests and makes this solution a real business enabler. Business owners can independently manage the remote access of external agents to the targets they are responsible for.

Minimised threat exposure
Remote Access contributes to zero-trust by managing yet not disclosing third-party user credentials, monitoring and recording of sessions, and the just-in- time mechanism. Remote Access mandates the usage of multifactor authentication (MFA) when accessing corporate networks.

Operational efficiency
Remote Access administration is done by business owners and does not require any technical prerequisites. Easily available for vendors, service providers, and other external users it does not require technical access or any IT engagement.

WALLIX IDaaS
Streamline access, fortify security, and elevate user experience across in-house or cloud applications. Our solution minimizes the risk of breach by integrating a Zero Trust framework, along with Single-Sign-On (SSO) and Multi-Factor Authentication (MFA).

Single-Sign-On (SSO)
It’s time to outgrow the “authentication-loop”, simplify employee workflows and improve productivity. With SSO, users can verify their identity once and seamlessly gain access to other applications.
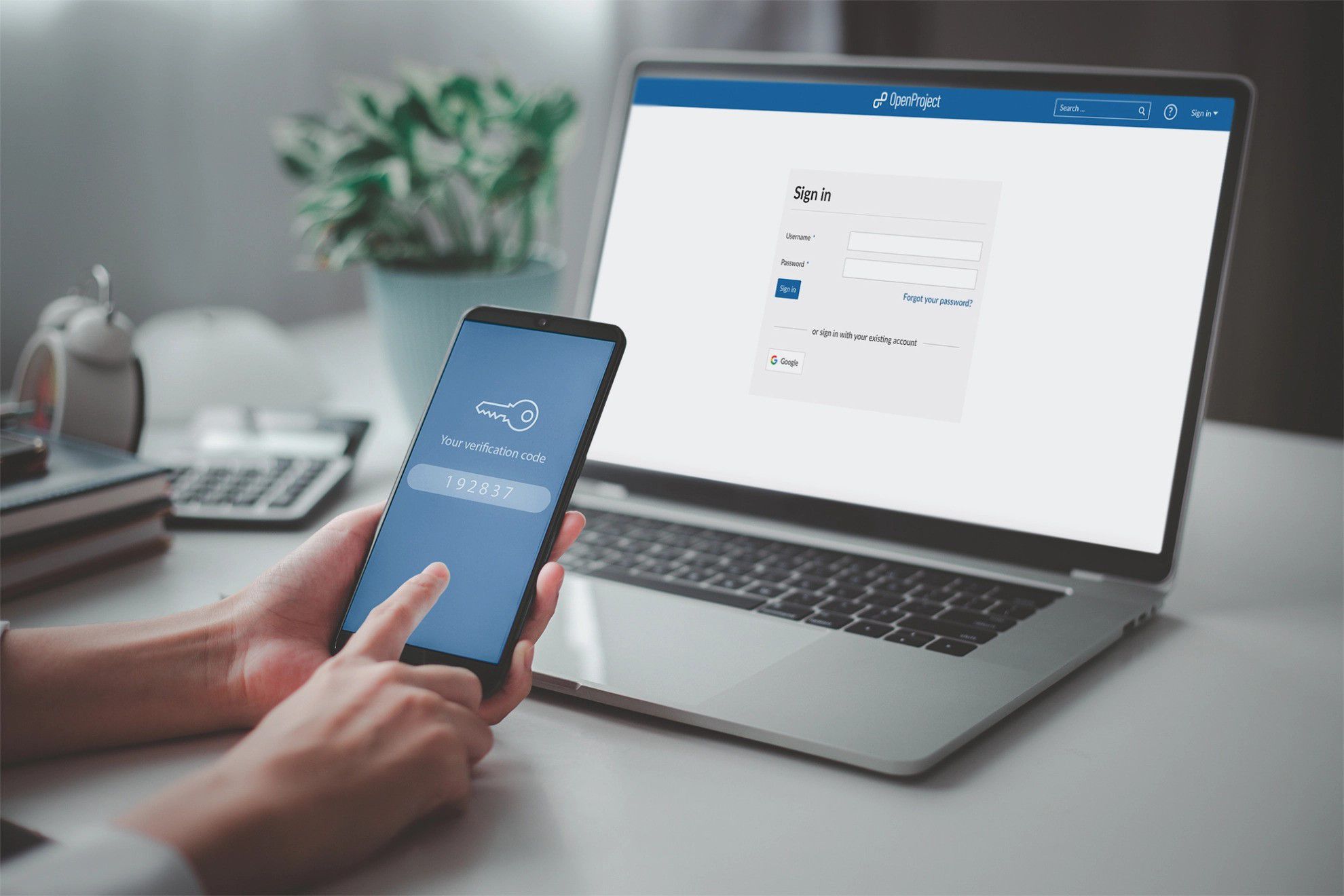
Multi-Factor Authentication (MFA)
By implementing MFA, you can secure accounts from credential theft and fraud.

Centralized User Acces Management
Empower your workforce and external users alike with seamless control over their data. Our system synchronizes users from corporate directories, automating access. External users benefit from self-service tools, including password resets and delegated administration, eliminating manual processes and saving IT teams’ valuable time.

WALLIX MFA
Strengthen Privileged Access Control with Multi-Factor Authentification
Zero Trust” Risk Management Policy
Take a “Zero Trust” approach to access security: multi-factor proof-based verification of a user’s identity provides the control needed to access corporate systems.

Unified, Secure, and Simplified Identification
Your users’ names and passwords can be hacked or cracked: using a multi-factor authentication solution increases authentication security. Eliminate password risks and have your privileged users use multiple credentials.

Native Integration with the WALLIX PAM security solution
Implement strong authentication for PAM. Enjoy seamless user experience as well as simple integration and maintenance for uncompromised security.
WALLIX IAG
Seamlessly provides a comprehensive mapping of identities to their respective permissions. Whether you’re overseeing access certification campaigns or tracking staff changes, our solution acts as a control tower for all your business applications.
Optimized Security
Since threat detection is automated to track and identify issues like orphan privileged accounts or over entitled accounts, your organization gains peace of mind enabling a secure environment where you can focus on your core business.

Compliance
In today’s landscape, meeting regulatory compliance is paramount for IT security and to avoid heavy fines associated with non-compliance. An Identity and Access solution helps you achieve better adherence to regulations, enabling meticulous risk management and streamlined auditing and reporting processes.